Incident Handling
This section will cover incident handling.
Table of Contents
- Definition and Scope of Incident Handling
- Cyber Kill Chain
- Recon
- Weaponise
- Delivery
- Exploit
- Installation
- Command and Control
- Action on Objectives
- Summary
Definition and Scope of Incident Handling
Incident Handling (IH) is an import part of an organisation defence, especially against cybercrime.
While protective and preventive measures are constantly implemented to lower the number of security incidents, incidents still do happen. This capability can be either in-house or outsourced to external parties.
Important terms:
- Event
- Incident
- Incident Handling
An event is an action occurring in a system or network. Some examples are:
- A mouse click
- A firewall allowing/denying a connection request
- A user sending email
- A user deleting files
An incident is an event with negative consequences. Some examples are:
- A system crash
- Data theft
- Funds theft
- Installation of malicious tools
- Floods
Incident Handling is a clearly defined set of procedures/processes to manage and respond to security incidents in a computer or network environment.
It is important to note that incident handling is not limited to intrusion incidents. Other types of incidents can be malicious insiders, loss/partial loss of availability, and more.
A comprehensive incident handling plan should address various types of incidents and the measures to identify, contain, eradicate, and recover from the incident and restore operations as quickly and efficiently as possible.
Cyber Kill Chain
The Cyber Kill Chain is one of many attack life cycles and frameworks. The Cyber Kill Chain was developed by Lockheed Martin. Understanding this life cycle can provide valuable insights on how far an attacker is and what they potentially have access to during the investigation phase of an incident.
The Cyber Kill Chain consists of seven (7) stages.
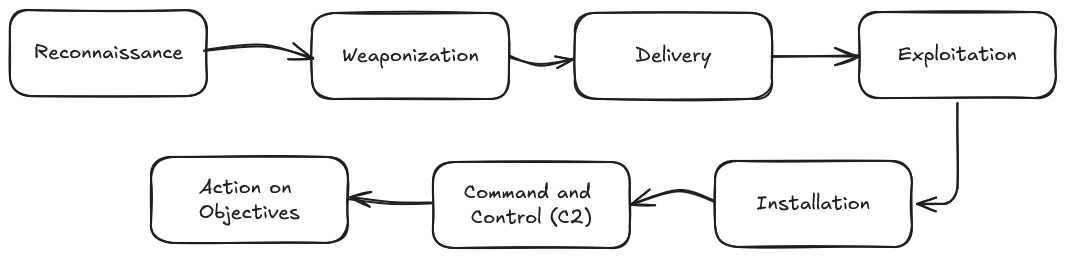
Recon
The reconnaissance stage is the initial stage. This is where an attacker choose their target and gather more information on their target to become more familiar with them. The goal of this stage is to gather as much useful data as possible that can be used in all stages of the Cyber Kill Chain.
Some methods can be passive reconnaissance where the attacker uses already public information such as LinkedIn or active reconnaissance where they start interacting with the target such as perform a Nmap scan.
Weaponise
The weaponise stage is where the malware that will be used for initial access is developed and embedded into a payload or exploit. It is likely that the attacker has gathered information on the EDR technology or defences used, making the malware lightweight and undetectable by the target defences.
On a large scale, the purpose of the initial access stage is to provide remote access to a compromised machine in the target network with potential persistence methods.
Delivery
The delivery stage is where the exploit/payload is sent to the victim(s). An example will be where it is sent via phishing where a malicious attachment is sent or sending a URL that mimics another website to trick the user into entering their credentials.
Exploit
The exploitation stage is where the initial stager is executed and is running on the compromised machine. During this stage, the attacker typically attempts to execute code on the target system to gain deeper access or more control.
Installation
The installation stage is where the initial stager is executed and is running on the compromised machine.
Some common techniques used in the installations include:
- Droppers - A dropper is a small piece of code that is designed to install and execute malware on the system.
- Backdoors - A backdoor is a type of malware that allows an attacker to gain persistence to a compromised system.
- Rootkits - A rootkit is a type of malware that is designed to hide its presence on a compromised system. A rootkit operates near or within the kernel of the operating system.
Command and Control
In the command and control (also known as C2 or C&C) stage, the attacker establishes a remote access capability to the compromised machine.
Action on Objectives
The action on objectives stage is the final stage of the attack. Depending on the objectives of the attacker, it can be exfiltrating confidential data or causing a disruption to operations.
Summary
It is important to note that attackers won't operate in a linear manner like in the Cyber Kill Chain.
An example will be where an attacker has gained initial access in the installation stage and is performing more reconnaissance to gather more information on the internal network.
The objective for defenders is to stop an attacker from progressing further up the kill chain, ideally at an early stage.